Protect Your Website Against XSS
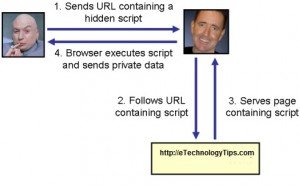
 XSS Attack (Cross site scripting) are very common attack found in web applications. Cross site scripting (XSS) vulnerability allows attackers to inject client-side script into a web pages and viewed by other users. Depends on how attackers use it, their effect may range from a mere nuisance to a significant serious security risk. Unlike another kind of attacks, Cross site scripting attacks are exclusive to web-based PHP applications and only have a little bearing on PHP applications type that are not accessible via internet. This article will show you how to protect your website against XSS attack.
XSS Attack (Cross site scripting) are very common attack found in web applications. Cross site scripting (XSS) vulnerability allows attackers to inject client-side script into a web pages and viewed by other users. Depends on how attackers use it, their effect may range from a mere nuisance to a significant serious security risk. Unlike another kind of attacks, Cross site scripting attacks are exclusive to web-based PHP applications and only have a little bearing on PHP applications type that are not accessible via internet. This article will show you how to protect your website against XSS attack.
XSS Types of Attack
There are no standardized types of XSS flaws. However, most people divide them into 2 groups.
- Persistent XSS attack, This type of attack is devastating, because it occurs when the malicious data provided by the attacker is saved by server. So it will be displayed permanently on normal web pages without proper HTML escaping. Persistent XSS attack can be more significant than another types of attack, because the attacker’s script is rendered automatically without needing to target individually or lure them to another website.
- Non-Persistent XSS attack, This type of attack is by far the most common type. Mostly, it occurs in HTTP query parameters or in HTML form submissions. Attackers injecting html script to the web pages which will be parsed by server immediately display that script to another user who accessing it, without properly sanitizing the request.
Identifying XSS Attack
An XSS attack is similiar to SQL Injection Attack. Both types of attack using user input that is not properly sanitized. The difference is SQL injection occurs when a field includes malicious SQL database query, while XSS occurs when a field contains malicious HTML script. The script are then run on another users computer. Any html tag that can load content from a remote source is vulnerable. Most common used html tag are <img>, <script>, and <embed>. Another tag can be used is <meta> (for cookie manipulation) and <base> (for rewriting every embedded object or script on web pages).
The most basic form is using <script> tag in the form input:
|
1
|
<script src="http://technotif.com/test.js"></script>
|
Before trying to detecting XSS attack, there are several things to remember :
- URLs can contain JavaScript (JS) and VBScript (VBS).
- HTML comments can easily confuse XSS detection and can be in most places in a document.
- Embedded object can have AllowScriptAccess set to true, which allows SVG images and flash accessing JavaScript.
- Parameters in HTML web pages dont need to be enclosed in quotes.
Prevent XSS Attack
Because this kind of attack is so complicated there is really only one easy way to prevent it. That is using htmlentities() to encode all HTML web pages. This will cause any HTML in user input to be displayed verbatim on the output page. The second best approach is to strip all HTML tags from input by filtering it using RegEx. However, both methods have their flaws. The first one is that neither will work in application where HTML tag needed to be allowed (such as rich text). The second method is a bit tricky. A good HTML stripping function can filter all of html tag. You can combine these two methods like this.
|
1
2
3
|
$filterhtml= preg_replace(‘/<script(?:\s(?:([“`\’])(?:\\\1|[^\1])*?\1|[^>])*)?’.‘>(?:.*?<\/script\s*>)?/g’‘’, $filterhtml);
$filterhtml = preg_replace(‘/<[^\s>]+(?:\s(?:([“`\’])(?:\\\1|[^\1])*?\1|[^>])*)?>/g’,‘’,$filterhtml);
$filterhtml = htmlentities($filterhtml);
|
First regex replace all script tag as well as content inside of them. Second regex replace all other tags while preserving the content inside them.














This is script injection, not XSS.
Thanks for the feedback jason kaler. One of the difference of script injection and XSS is the purpose of attack. If it’s targeting the webserver application then it’s called script injection. otherwise, if it’s targeting the user who accessing the webserver it’s called XSS. CMIIW