Encoding is a process of converting data from one to another form. Encoding data so that it cannot be easily read is one of the key tenets of security. A good secure system not only takes measure to prevent data from being exposed but also ensure...
Encoding Decoding Data Using PHP



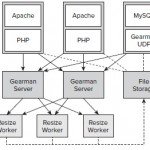
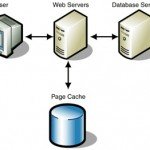








Latest Comment