Prevent SQL Injection by Using Runtime Protection
In this article, we will consider runtime protection to prevent SQL Injection that is deployable without recompiling the application’s source code. Mainly covered here are software plugins for Web Servers and application frameworks (For example .Net Framework, PHP, J2EE, etc.). The software solutions we will discuss are open-source (Free) and available for download on the Internet. Although there are many commercial solutions to Prevent SQL Injection, We will not cover this as commercial products.
Runtime protection is a tool / software for migrating and preventing exploitation of known SQL Injection vulnerabilities. Fixing the application’s source code is always an ideal solution. However, the required condition is not always feasible. Even if resources and time are available to fix the source code, runtime protection still be a good layer of security to detect and prevent exploitation of unknown SQL Injection vulnerablities. There’s also threat named “zero-day” exploit techniques as well as the latest SQL Injection worm transversing Internet. In this way, runtime protection not just act as reactive defense mechanism, but also proactive through securing an application.
Eventhough this kind protection provides many benefits, it’s costs too much. Depending on the solution, there are some level of peformance degradation aftereffect. When you consider a solution, especially a commercial one. It’s important to know about documented peformance statistics. The key to get the most out of runtime protection is a willingness to know the limitations of technology.
Web Application Firewalls to Prevent SQL Injection
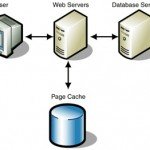
There are many solution of using runtime protection. One of them is Web Application Firewalls (WAF). WAF is a software-based solution that adds security layer features to a web application. Spesifically, WAF can protect web application from SQL Injection.
 Benefits of using software based WAFs are that HTTP/HTTPS communications are handled seamlessly, and the web application remains unchanged because they run inside application hosting process or inside the web. WAFs which based on appliance do not consume web server resources and they can protect multiple websites of varying technologies. But we will not cover that in this article. Although you can use some solutions as a network appliance when running on a reverse proxy server.
Benefits of using software based WAFs are that HTTP/HTTPS communications are handled seamlessly, and the web application remains unchanged because they run inside application hosting process or inside the web. WAFs which based on appliance do not consume web server resources and they can protect multiple websites of varying technologies. But we will not cover that in this article. Although you can use some solutions as a network appliance when running on a reverse proxy server.
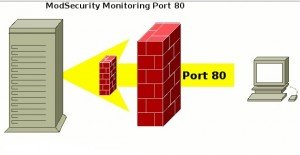
Using ModSecurity to Prevent Attack
The standard for WAFs is the open source ModSecurity. it is implemented as an apache module. However, it can protect any Web Application when apache is configured as a reverse proxy. You can use it for monitoring, intrusion detection, attack prevention, prevent SQL Injection and general application hardening.