Finding Vulnerabilities In Network Systems
After you find out target’s network configuration using port scanner, You need to know what is your target’s weakness. You can step further by testing and see which vulnerabilities really stand out. Finding vulnerabilities in network systems is not hard to do. There are various software tools that can help you finding vulnerabilities in network systems such as
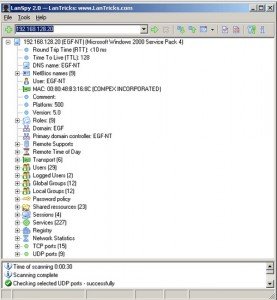
- LanSpy, set of network utilities combined into a single program and it’s easy to use. LanSpy includes network port scanner too. LanSpy runs on windows platform.
- Nessus, an open source network and OS vulnerability-assessment tool. Nessus runs on Windows and Linux platform.
- Amap, an open source linux and windows-based mapping tools. fast and reliable mapper.
- GFI LANguard Network Security Scanner, a Windows-based tools for performing network and OS vulnerability assessment. But it’s not free (Commercial).
- QualysGuard, it’s an application service to find vulnerabilities on network and Operating System.
You need these tools to do security testing on network. the more you can test the bigger chance you can get network target’s weakness. That’s why it’s so important to get personal firewall and IPS software like BlackIce (for Windows) and Gnome Lokkit (for Linux).
Common Access Point Weaknesses
Wireless Access Point are wireless client with insecure operating systems just like any other device. There are many ways for finding vulnerabilities in network systems, one of them is to use a vulnerability assessment tools like Nessus, QualysGuard, or GFI LANguard. Common Access Point’s vulnerabilities such as, SNMP issues, Weak version of SSH, SSH banner information, and Open UDP and TCP Services are not critical, but at least these information need to be addressed because they can lead to further AP and network compromise.
Mapping Application on Linux
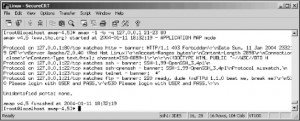
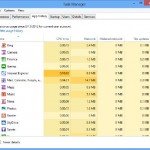
When dealing with linux client security, most common attack against application using known security vulnerabilities. These include FTP, Apache, Sendmail and telnet. These vulnerabilities can be determined through application mapping. We can do application mapping easily by using Amap.
Amap is a good application scanner for pentesters. It can identify applications even if they are running on a different port than normal (For example, when apache is running on port 1671 instead of its default port 80). Amap can extract version information. You can notice from the image that SSH, telnet, and FTP server were discovered. That’s an example output of an Amap scan run against local host.
Most Known Vulnerabilities on Windows
Windows Null Session, Vulnerabilities on Windows that can map an anonymous connection to a hidden share called interprocess communication (IPC). This attack method can be used for gathering windows information like Share names, User ID, even allow the attacker to edit computer’s registry.
By default, Windows 2003 and Windows XP don’t allow null session connection. But Windows NT and Windows 2000 systems allowed it, so you have to protect yourself by testing all your wireless client.
How to Map a Windows Null Session
To map a windows null session. You can use these steps :
- Go to Start >> Run >> Type cmd >> enter
- At command prompt, type net use \\hostname_or_ipaddress\ipc$ “” “/user:”
- Press enter.
I will explain that command parameters.
- Net Use : Connects, Disconnects, or Display an information of a computer from shared resource.
- hostname_or_ipaddress : Ipaddress or hostname of the system which you want to map.
- “” “/user:” : A blank password and Username (Null Connection)
By using a null session connection, you can gather critical windows information or get data from windows shares ( if they used default configuration ).