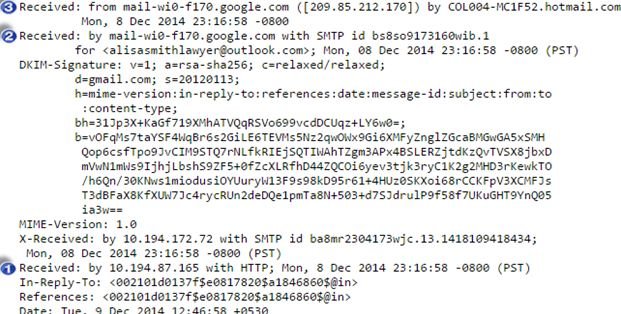
Email Header Forensic Analysis
Technology has certainly made doing things way easier than it was ever before. As a result, not only tasks but also the rate of technological crime has increased relatively. The easier it is to communicate nowadays, the simpler it is to fool someone around. An email consists of three major components, i.e. envelope, message header, and body. Email header is the most primary source of information out of all these elements.
There are plenty of ways to detect forgery of information in an email but they are all associated with the header examination. Spoofing of header not only involves hiding the true information from recipient but also displaying misleading set of information.
The execution of such activities however, takes place through a number of different mediums. The post discusses some of the methods that help in spoofing information of the email header to baffle the user in discovering the original identification of the sender. A number of techniques are used for the same and some of the most common one’s have been listed below.
Forensically Investigating Email Header
Spoofing email messages, identity, or header information is easier now days, thanks to techniques like message relay, botnets, and open proxy. Here is a list of such technologies adopted by online users that open doors for them to achieve their deceitful desires effortlessly. As a result, a rapid increase in the requirement of email header forensic analysis is encountered to detect illegitimate acts.
Such acts are known as phishing, transmission of malware, cyber bullying, spamming, or web infrastructure based criminal acts (conducted via DoS and DHA or Directory Harvesting Attacks).
Consequences of Such Acts: Acts as injudicious as these result in the occurrence of several technological troubles involving issues like; computational resource being wasted, misuse of storage, conjunction of network, and more. A highly qualified spammer can easily evade packet data filters to manipulate an IP address, portraying their message to be coming from a trusted domain.
Techniques Commonly Used for Spoofing
- Spoofing: This technique is implemented by users for hiding the real identity of a message sender by manipulating its header details. This technique is also used in combination with spoofing of IP address, which further complicates the process of detecting the culprit.
- Open Mail Relay: The technique is simply a mis-configured email relay service. This allows messages from any source machine and sends them further to other computers, which are supposed to accept messages from and for only a particular set of computers. These relays become easy targets to phishers and spammers hiding their identity through the relays.
- Remailers: The websites operating in the guise of keeping internet privacy for users by extending the option of browsing the web anonymously are known as remailers. They purposely strip off the header portion of emails and keep off from maintaining server logs.
- Botnets: Bots is a term derived from ‘Robots’. Botnets, in generic form are script(s) or program that has been designed for carrying out a set of predefined functions. These predefined functions are performed automatically and repeatedly after being targeted through an infection on the system or by intentional means. Originally developed as an option to execute time taking repetitive tasks however, later started being misused for deceitful purposes. Bots were started being used for illegitimate intents where the network is operated by a botmaster. The master commands malicious bots under its control to transmit messages to addresses without revealing its genuine identity in the process as part of committing email based crime.
- Open Proxy: It is a machine acting as a medium one computer to connect with the other one to browse the internet. These servers are HTTP based and provided by a number of proxy server types like; Corporate Proxy Server, transparent proxy, Internet Service provider, as well as open proxy which is better known as the anonymous proxy for the anonymity of users at different levels. When connecting to the web via these servers share IP however, an open proxy is against maintaining user activity log. Therefore, providing anonymity to users making it next to impossible to trace the internet activity they have been carrying out.
- Shared Internet: While offering shared internet connection via access points such as universities, café or food joints, or cyber cafés, offices, etc., it is very important to keep log of user activities. Otherwise, it becomes very difficult to detect the culprit behind any malicious activity carried out using the shared internet service.
Such techniques when used in any combination can lead to a lethal output where the senders can keep themselves from revealing their identity and carry out illegitimate activities openly. However, specialized email header forensics analysis expert can easily spot and deal with such manipulations during the investigation of emails.
Conclusion: A dedicated examiner can easily detect spoofing of information in email headers whether in the form of IP, sender details, received from ID, domain, or more. A thorough examination involves the study of source as well as destination of the email along with the devices used as a medium to deliver the message.
To check the legitimacy of email when common approaches like botnets, open relay, remailers, etc., are applied to gain anonymity in cyberspace. However, automated header analysis performed by the software programs is more preferred by investigators these days to analyze the header automatically for any kind of information manipulation. One such commercial utility is MailXaminer built with 7+ advanced email header and body analysis modules. The application features several other supporting features as well that help in executing email header analysis in a comparatively organized, accurate, and streamlined manner.